Netflix 2006 CSRF Issue
Netflix 2006 CSRF Vulnerability
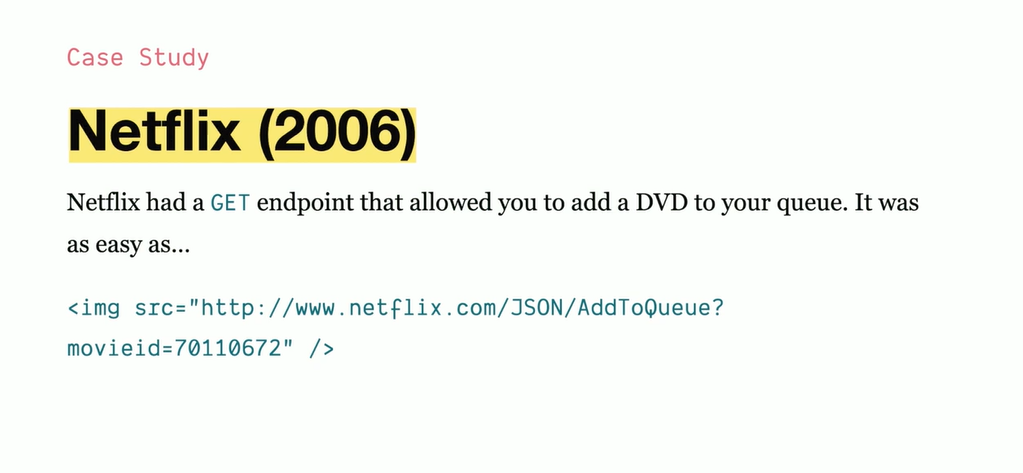
In 2006, Netflix was found to be vulnerable to a Cross-Site Request Forgery (CSRF) attack, allowing attackers to manipulate user accounts without their consent. The issue was publicly disclosed by security researcher Jasper Greve.
What Was the Vulnerability?
- Netflix’s web application did not use CSRF tokens to verify user actions.
- An attacker could craft a malicious request to perform actions on behalf of a logged-in user.
- If a user visited a malicious webpage, the attack could modify their Netflix account settings (e.g., change queue preferences, add/remove movies).
How Did the Attack Work?
-
User Logs into Netflix
- A user logs into Netflix, and their session cookie is stored in the browser.
-
User Visits a Malicious Website
- The attacker tricks the user into visiting a webpage with a hidden CSRF attack payload (e.g., an
<img>or<iframe>tag).
- The attacker tricks the user into visiting a webpage with a hidden CSRF attack payload (e.g., an
-
Malicious Request is Sent to Netflix
-
The website silently sends an unauthorized request to Netflix using the victim's active session.
-
Example of a hidden attack:
<img src="https://www.netflix.com/Queue?add_movie=12345"> -
This would automatically add a movie to the victim’s queue without their knowledge.
-
-
Netflix Accepts the Request
- Since Netflix did not verify requests with CSRF tokens, it processed the request as if the user had performed the action.
- The victim’s account was modified without their consent.
Why Was Netflix Vulnerable?
-
Lack of CSRF Tokens
- Netflix did not require a CSRF token in requests, allowing attackers to submit forged requests.
-
Session Cookies Were Automatically Sent
- Since Netflix used cookies for authentication, browsers automatically sent them in cross-site requests.
- No
SameSiterestrictions were in place to block CSRF attacks.
-
GET Requests Modified State
- Actions like adding movies were performed using GET requests, which should only be used for reading data, not modifying it.
Impact of the Vulnerability
- Attackers could manipulate users’ movie queues.
- If combined with XSS, attackers could have gained full control over accounts.
- Netflix had to quickly patch the issue to prevent large-scale abuse.
How Netflix Fixed It
✔ Implemented CSRF Tokens:
- All state-changing requests now require a unique CSRF token to verify authenticity.
✔ Switched to POST for Modifications:
- Actions like adding movies now require POST requests instead of GET.
✔ SameSite Cookie Enforcement:
- Netflix improved session security by implementing
SameSite=Laxcookies to block cross-site requests.
✔ Security Best Practices:
- Netflix now follows OWASP security guidelines, including input validation and session security improvements.
Lessons from the Netflix CSRF Issue
🔹 Always use CSRF tokens in forms and API requests.
🔹 Restrict session cookies using SameSite=Lax or Strict.
🔹 Never allow GET requests to modify user data—use POST or PUT instead.
🔹 Regularly test for CSRF vulnerabilities in web applications.
The Netflix 2006 CSRF issue was an early wake-up call that even large platforms need strong CSRF protections to prevent unauthorized actions. 🚀