XSS - The Samy worm 2005

The Samy Worm (2005) – The First Major Social Media Worm
The Samy Worm, also known as the MySpace XSS Worm, was a self-propagating cross-site scripting (XSS) attack created by hacker Samy Kamkar in 2005. It became one of the fastest-spreading internet worms and led to over a million MySpace profiles being infected in less than 24 hours.
How Did the Samy Worm Work?
-
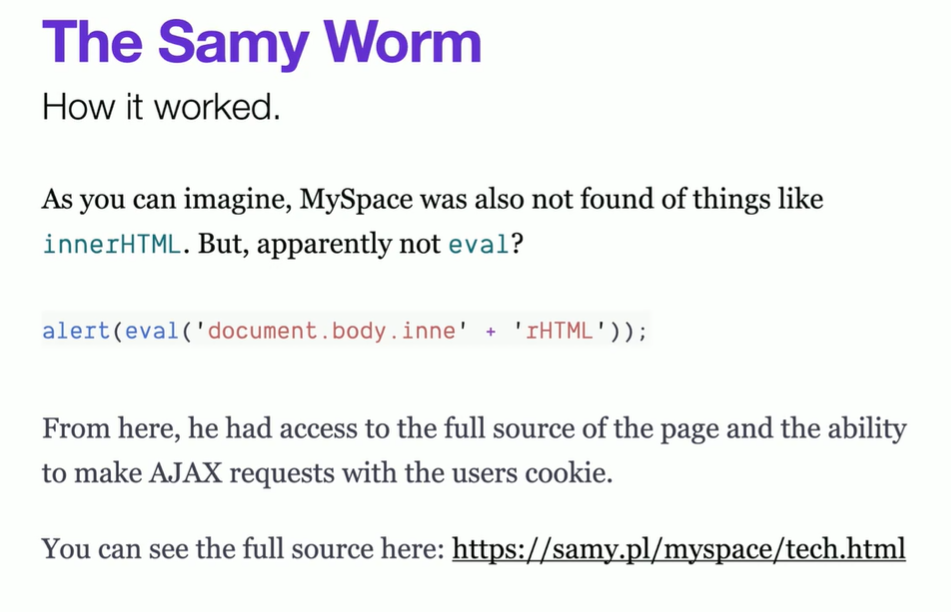
Exploited a Stored XSS Vulnerability
- MySpace allowed users to embed custom HTML and CSS in their profiles.
- JavaScript was supposed to be blocked, but Samy found a way to bypass this restriction.
-
Injected Malicious JavaScript
- Samy added JavaScript payload inside his MySpace profile’s "About Me" section.
- This script executed automatically when anyone visited his profile.
-
Self-Replication (Worm Behavior)
- The script copied itself onto the profile of anyone who viewed Samy's profile.
- Those infected users unknowingly spread the worm when others visited their profiles.
-
Displayed a Harmless but Viral Message
-
Infected profiles showed the message:
but most of all, Samy is my hero
-
-
Exponential Growth
- Every infected user infected their visitors, leading to over 1 million profiles affected within 24 hours.
Technical Breakdown of the Attack
- Samy used XSS (Cross-Site Scripting) to execute JavaScript inside MySpace.
- He bypassed MySpace’s script filters by using CSS and JavaScript obfuscation.
- The worm exploited XMLHttpRequest (AJAX) to automatically send friend requests and update profiles.
Samy's Payload (Simplified)
<script>
var ajax = new XMLHttpRequest();
ajax.open("POST", "/addfriend.php", true);
ajax.send("friend_id=12345");
</script>
- This code sent friend requests to Samy automatically.
- It replicated itself to every visitor’s profile.
Impact of the Samy Worm
🔴 Over 1 million MySpace users were infected in a day
🔴 MySpace had to shut down for hours to remove the worm
🔴 Samy Kamkar was investigated by the U.S. Secret Service and FBI
🔴 Samy was banned from using computers for three years as part of his plea deal
How MySpace Fixed It
✔ Sanitized User Input:
- MySpace properly filtered JavaScript from profile inputs.
✔ Implemented Content Security Policy (CSP):
- CSP rules were enforced to block inline JavaScript execution.
✔ Limited User-Generated Content Capabilities:
- MySpace restricted custom HTML and JavaScript in profiles.
✔ Security Awareness Increased:
- The attack raised awareness of XSS vulnerabilities, influencing future security measures.
Lessons from the Samy Worm
🔹 XSS is a serious security risk that can be self-replicating (wormable).
🔹 Always sanitize and escape user input to prevent JavaScript injection.
🔹 Use CSP and proper HTTP security headers to block malicious scripts.
🔹 Never assume input validation is enough—attackers find creative bypasses.
Final Thought
The Samy Worm was the first major XSS-based internet worm, proving that client-side vulnerabilities could lead to massive security breaches. 🚀